Can a Screen Lock Pin Keep a Keylogger Out of My Phone

December 3, 2021
Think about everything you lot do on a figurer or phone in a given day. Yous might compose work emails, sign in to
social media, chat with friends, search for information, check your bank account, shop for products — things so ordinary you may not even remember them all.
Now imagine finding out someone had been hiding behind you, watching every single primal you typed.
Keylogging, also known equally keystroke logging, is the deed of recording a user's keyboard interactions and device activity. Though it tin be performed legally, it's also a grade of information monitoring that hackers and identity thieves employ to acquire people's personal data. There may not exist anything inherently unethical well-nigh a keylogger, but in the easily of a malicious user, a keylogger tin crusade serious damage.
Keylogger-based malware has become another dangerous weapon in cyberattackers' arsenals. It'due south important to sympathise what a keylogger is, how to spot one, how to prevent keylogging malware, and how to secure your personal data.
What is a keylogger?
A keylogger (or keystroke logger) is a type of software or hardware used to track and record what someone types on their keyboard. Keyloggers can exist used legally (some people fifty-fifty install them on their ain devices), and you may have even used a reckoner with software installed to log keystrokes for monitoring and ensuring condom or approved use.
Merely what keylogging ways for everyday users is very different from what it ways for cybercriminals. Malicious actors can besides utilize them to capture your personal and financial information, PIN codes and account numbers, credit carte du jour numbers, usernames, passwords, and other sensitive information — all of which tin can be used to commit fraud or identity theft.
How keylogging works

Keystroke trackers are readily bachelor, and there may be one installed on the very device you're using to read this. The software itself isn't necessarily problematic if y'all signed an understanding to utilise the device information technology'due south installed on or if it was packaged in your device's software suite. What makes these tools problematic are bug of actor intent and victim consent.
Whether the employ is legal or illegal, all keylogging mechanisms work essentially the same way. They record every keyboard interaction a user has, allowing a third party to run into a complete log of every e-mail, instant bulletin, search query, password, username, or other keyed sequences that user types. Keystroke malware comes in a diverseness of forms:
- Phishing emails: Past clicking a link or downloading an zipper in a phishing email, text bulletin, instant message, or social media post, you could accidentally download malware designed to track keystrokes.
- Trojan viruses: Named afterwards the giant wooden horse Greece used to infiltrate Troy during the Trojan War, hackers trick users into downloading a Trojan virus by disguising it as a legitimate file or application.
- Zero-twenty-four hours exploit: A zero-day exploit happens when hackers discover latent software security flaws and apply them to deliver malware through tactics like malicious webpage scripts and Trojans. Developers acquire of the vulnerabilities too late to protect users. These are peculiarly dangerous because once the systems are infected, they so become more than susceptible to further attacks.
- Infected systems: Keyloggers tin can take reward of an already-infected device or system and install other malicious software into that system.
Keylogging malware can infect your estimator through many of the same mechanisms every bit other mutual viruses, simply information technology can also be intentionally purchased and downloaded. In short, keyloggers tin either be tools or weapons, depending on who is installing them and how they're using the acquired information.
Types of keyloggers
For the general public, keyloggers are most ordinarily spread online via phishing scams, Trojan viruses, and simulated websites. Hackers' main goal is to obtain victims' passwords, personal information, usernames, and cyberbanking data, enabling them to make bank transfers, open credit lines, and brand purchases. Malicious keylogging mechanisms break down into two broad categories: software and hardware.
Software-based keyloggers
Many software-based keyloggers have rootkit functionality, meaning they're able to hide in your system. These Trojan-spy programs can track your activity (including keystrokes and screenshots), save the data to your hard disk, and and then forrard the information to cybercriminals. Some of them are also able to rails everything from information copied to your clipboard to location data and tin can even tap your microphone and camera. These tools tin reach you at a few different levels:
Kernel level: These are complex and difficult to write, so they aren't specially common. Once installed, keyloggers affecting your device at the core of its operating system are especially hard to diagnose and eradicate, as they've substantially been handed the "keys" to your device.
- Application programming interface (API) level: The virtually common form of keylogger software intercepts signals sent from your keyboard to the program a user is typing into. Think of it like a recording device waiting between your physical keyboard and a program on your computer screen, similar a word processor or browser.
- Screen level: Known as "screen scrapers," these types of keyloggers take regular screenshots, recording what appears on the user'south screen.
- Browser level: This is the least circuitous and least deeply rooted of the four types, simply it can still be quite dangerous. This "course-grabbing" ploy records what you type into webforms, which may include everything from Social Security numbers to contact information to login credentials.
Keylogging software is much more mutual than keylogging hardware because information technology's discrete, can be packaged every bit malware, and is readily available today from online vendors. Notwithstanding, hardware-based keyloggers are all the same used for a variety of reasons and should not be ignored.
Hardware-based keyloggers
These keystroke loggers have a physical component to their implementation, either in the wiring or hardware of a device or in the setting around it. A mutual case of a hardware-based keylogger is the keyboard overlay on an ATM. Every fourth dimension a bank customer presses the buttons on the criminal's fake keypad — thinking it'southward the legitimate ATM keypad — the keylogger records the keystrokes and forwards the information to the cybercriminal.
These keyloggers tin't be detected by antivirus software because they aren't installed on the computer, and they utilise their own internal memory to store and encrypt data. There are several general types of hardware-based keystroke loggers that range in their sophistication:
- Keyboard: These keyloggers are installed either in the wiring connecting a keyboard to a computer or direct in the keyboard itself.
- Physical drive: Keylog Trojans in this category are typically delivered via a USB drive or Mini PCI card.
- Third-party recording: The to the lowest degree sophisticated form of keylogger attack is an external recording device like a camera, which can exist strategically placed to monitor public keypads or computer keyboards.
- Acoustic: This rarely used method of keystroke monitoring records the almost imperceptibly distinct sounds made when the individual keys of a keyboard are struck.
While keylogging hardware may not be as common equally its software-based analogue, it can still be highly dangerous and can compromise vital data.
What are keyloggers used for?
In some form or another, keyloggers accept been in use for decades, harkening back to covert KGB operations in the 1970s. Today, keyloggers are the sixth most mutual form of enterprise malware, but they are also often packaged within the most common type — a downloader — as office of a suite of Trojan viruses.
But is a keylogger illegal in and of itself? Not necessarily. Here's how legal usage breaks down.
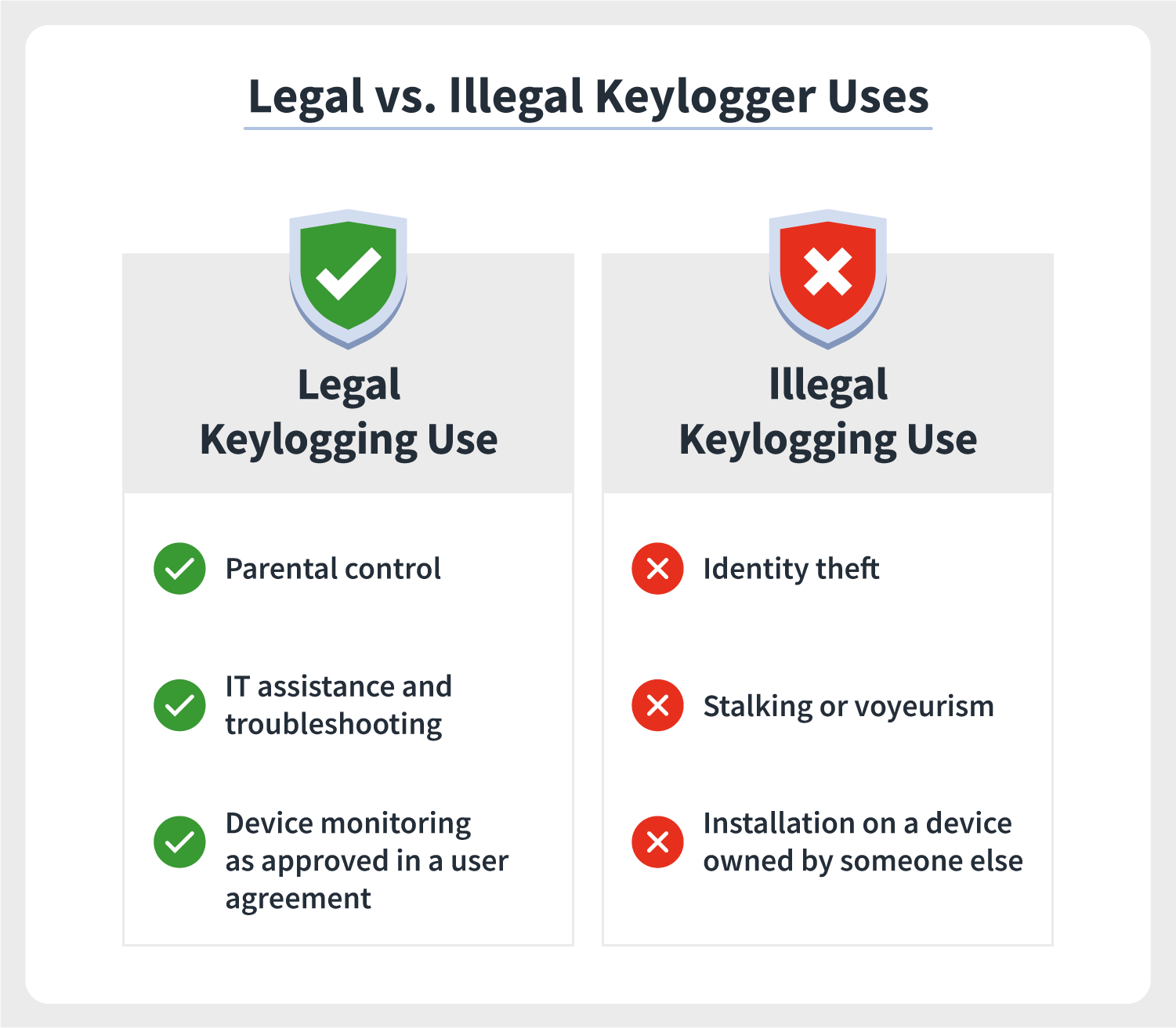
Legal keylogging examples
The legal use of keyloggers depends on user consent (depending on local laws), whether they're used maliciously to steal personal information, who owns the devices they're installed on, and whether the use victimizes someone in a manner that breaks any other applicative law. Here are a few examples of potentially legal keylogging:
- User experience data monitoring
- Parental control to monitor and protect children's online activity
- Recording usage on a personal device owned past the keylogger user
- Network, software, or hardware troubleshooting
- Company data exchange and search query monitoring
- Devise-utilize monitoring by a visitor or public entity, such as a library
- Any legal usage consented to via a user agreement or contract
Essentially, legal use comes down to local laws, user consent, and no intent to misuse user information.
Illegal keylogging examples
Illegal keylogging gets catchy because sometimes potentially legal usage can straddle the line betwixt unethical and illegal. More often than not speaking, the use becomes illegal primarily when it leads to stolen confidential data or when software/hardware is installed on a device owned by someone else, as outlined below:
- Account information theft
- Drove of sensitive information
- Monitoring when consent was explicitly denied via a legally bounden contact
- Credit card data and Pin collection
- Installation of software or hardware on someone else'due south device
- Keystroke monitoring of a public device
- Unlawful stalking or voyeurism
In general, what makes keylogging illegal is a lack of user consent or the utilize of keyloggers on someone else's belongings, though specific laws on usage can vary by location.
The threats of keyloggers
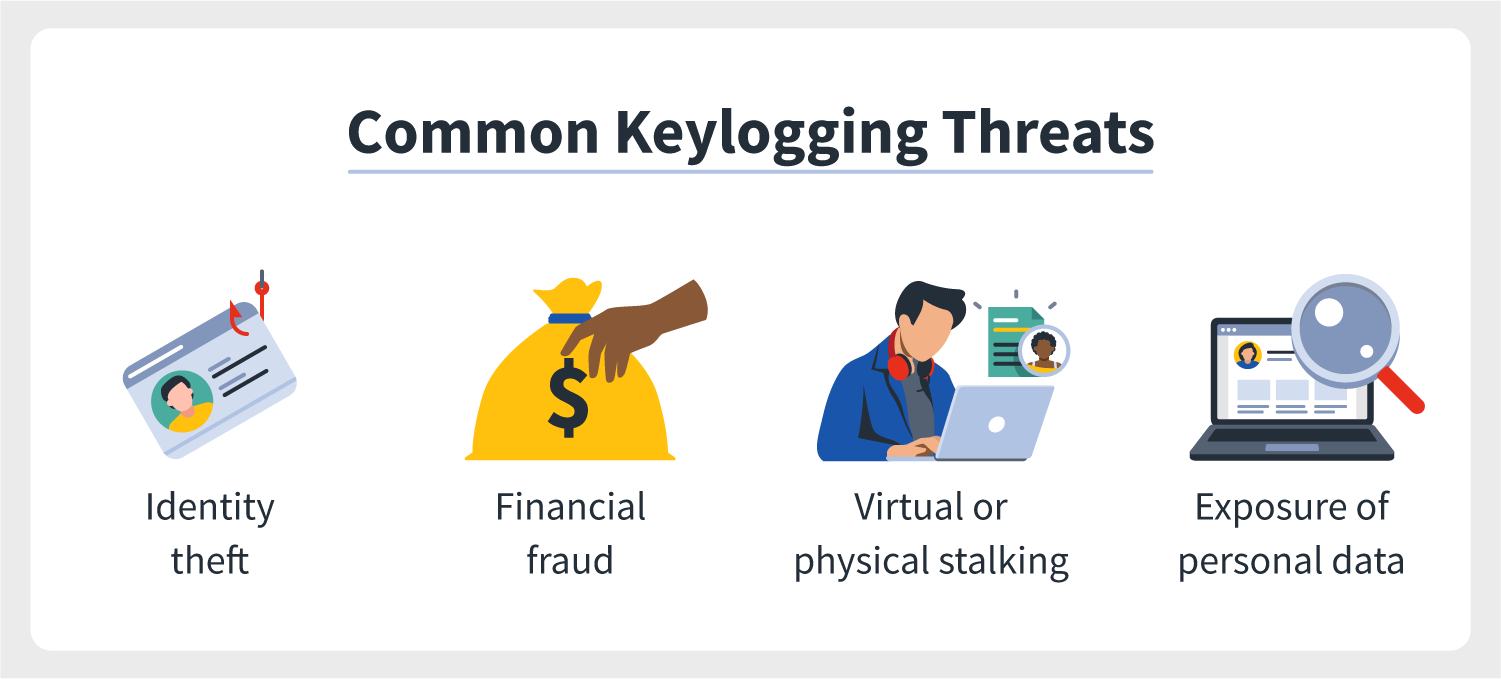
Cybercriminals may exist able to record and utilise everything you type. No matter how secure you believe your devices are, a keylogger hack represents a major threat to your cybersecurity because cyberattackers can weaponize some of your common virtual activities without your noesis. A lot of information can be gathered from what you enter on your devices via your emails, text messages, login credentials, and web browsing.
Every bit noted above, cybercriminals may use keylogging malware for more overtly dangerous information like bank account numbers, PINs, or Social Security numbers, but they tin as well steal more personally sensitive content like browsing data, conversations, and fifty-fifty video or audio recordings. After cybercriminals admission this information, yous could be susceptible to whatever of these threats:
- Fiscal fraud
- Identity theft
- Information ransom
- Virtual or concrete stalking
- Voyeurism and eavesdropping
- Credit bill of fare, checking, or other financial business relationship lockouts
- Exposure of sensitive personal information
This is in no way an exhaustive list of the ways in which keylogging can be used confronting you. It's vital to protect your methods of accessing, transferring, and recording your data so you can mitigate these and more keystroke-monitoring threats.
How to prevent keylogging

To help protect yourself from keylogger malware, follow full general online safety all-time practices and maintain a healthy sense of skepticism when engaging in any online activity. Malicious keylogger protection is like to most forms of virus protection, but no solution is foolproof. New malware is beingness written all the time, but here's how to prevent keylogging attacks as much every bit possible by reducing your hazard of encountering malware.
Enable two-factor authentication
2-gene authentication is 1 of the most effective forms of virus, malware, and keylogger prevention. Too known as 2FA, this solution adds an extra log-in stride such as a fingerprint or temporary PIN sent to your phone, helping verify that the person logging into your business relationship is really you. Enable 2FA whenever you can to help ensure that if your data is stolen, cybercriminals can't sign into your accounts remotely.
Don't download unknown files
The next best manner to protect yourself from malware is to refrain from downloading any unknown files and avert strange links birthday. Phishing attacks are getting more sophisticated, but be skeptical of anyone—even contacts y'all know—telling y'all to download attachments or click links out of the blue.
Consider a virtual keyboard
This solution displays an interactive keyboard on your screen so y'all don't have to physically type on an analog one. While a virtual keyboard isn't an airtight prevention tactic, it does circumvent keylogging hardware and any keylogging software specifically designed to tape interactions with your physical keyboard. Some software can however monitor your on-screen interactions, all the same, so this should exist seen as a supplemental tool and not a complete solution.
Employ a password manager
Password managers are not just user-friendly ways to ensure you don't forget the seemingly endless number of logins we all take to juggle these days — they're also great keylogger protection. By logging in with a password managing director, yous don't display your passwords or physically type them, then keystroke monitors can't capture them.
Install antivirus software
Await for antivirus software that includes anti-spyware and anti-keylogger protection. As with all forms of viruses, new, more sophisticated keystroke malware is beingness written all the time, so exist sure to go along your software upwards to date to stay secure.
Consider voice-to-text conversion software
Similar to a virtual keyboard, vocalisation-to-text conversion software can circumvent forms of keylogging that specifically target your physical keyboard.
How to discover and remove keyloggers
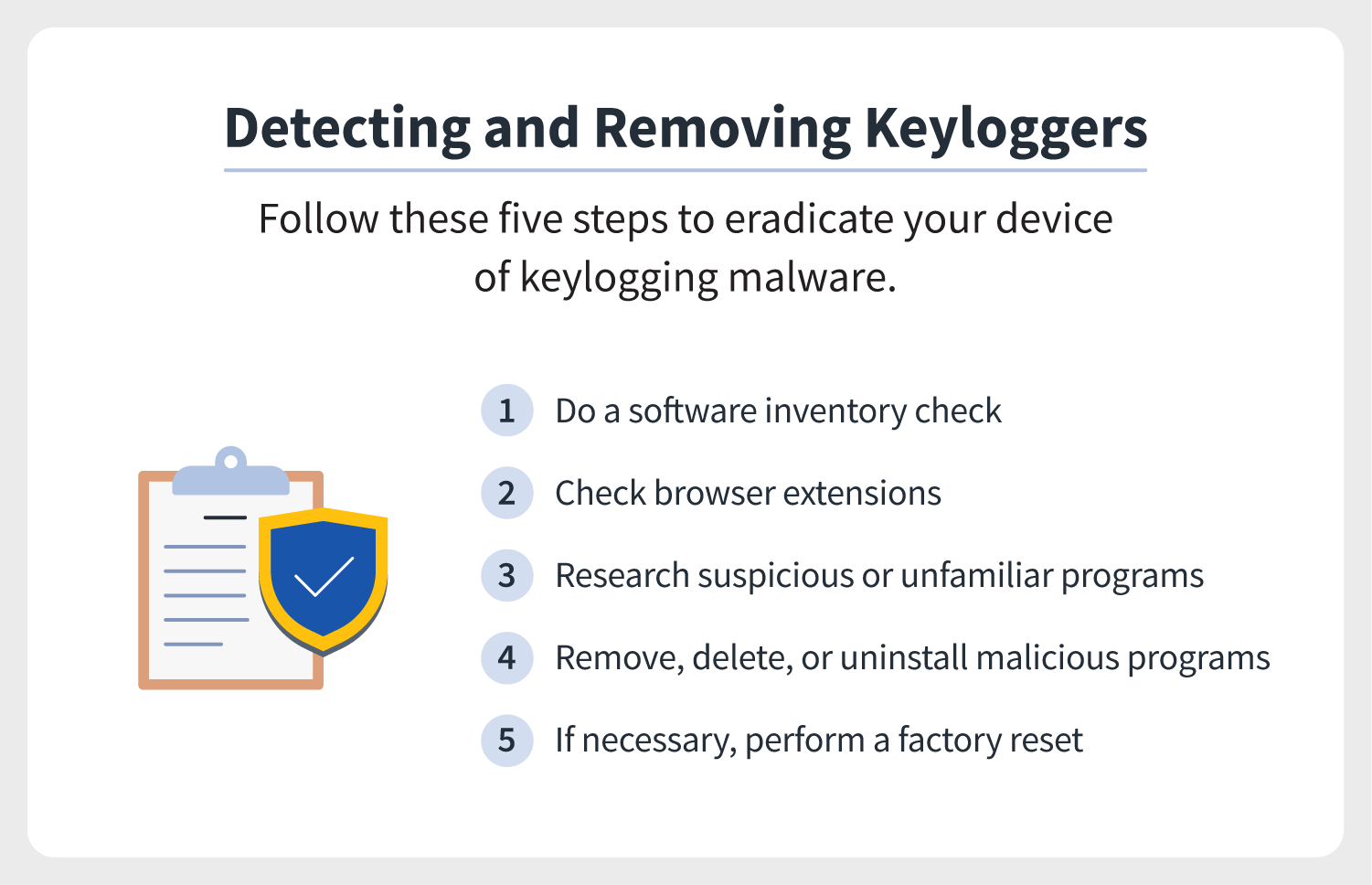
Keystroke monitors thrive on stealth, simply can a keylogger be detected? While hardware may be relatively easy
to find — a USB drive or extra piece continued to your keyboard wire — software tin often go undetected until it'due south too late.
Keylogging malware may show many common virus warning signs, including slower computer performance when browsing or starting programs, aberrant delays in activity, pop-ups, new icons on your desktop or system tray, or excessive hard bulldoze or network activeness. If yous detect any of these, yous may want to follow the steps below to identify and remove keylogging malware.
1. Do a software inventory check
Successful keystroke logger detection starts with taking stock of the programs and processes running on your estimator. While many of these may have unfamiliar or even suspicious-looking names, they may blend in with the names of other software.
two. Practise a browser extension bank check
Some keylogging malware is designed specifically to monitor your spider web usage and may show up as a browser extension. Cheque your browser menu and navigate to the list of agile extensions. If there are any yous don't recognize or never downloaded, deactivate and remove them.
three. Remove keyloggers
Keyloggers tin can be removed in much the same manner you lot would remove other forms of malware. You should always exercise extreme circumspection when handling reckoner programs. Even if a program seems suspicious, information technology could exist a necessary tool, and disabling it could cause problems. Once you've identified a program you're 100% sure is a keylogger, disable, uninstall, and/or delete information technology from your device.
4. What to practice if you don't find a keylogger
If you neglect to place whatever malicious keyloggers but still want to make absolutely sure your device is free of malware, you lot could reinstall your device's operating system or perform a factory reset, which volition finer wipe all the information and programs from your device that were installed across the factory defaults.
In a perfect world, you'll never need to know what keylogging is. But the reality is that today, there are many
malicious cyberattackers out there trying to trick as many people as possible into downloading malware like a keylogger. It'due south vital to practise safety internet use and protect your sensitive information.
Keylogger FAQs
Below are answers to some of the most ordinarily asked questions regarding keyloggers.
What is a keylogger?
A keylogger is software or hardware designed for monitoring and recording a user'south interactions with their keyboard and the associated device.
What does a keylogger do?
A keylogger surveils what someone types on their keyboard, recording their interactions with browsers, word processors, webforms, and other text-based media.
What are keyloggers used for?
Keyloggers are used to monitor how a user interacts with their keyboard equally a means of recording their behavior, usage, or personal information.
Is a keylogger illegal?
While keylogging tools are not illegal in and of themselves, they are often used in an illegal mode by cyberattackers, identity thieves, or other malicious users to surreptitiously steal information or track activity without user consent.
What is the history of keyloggers?
Early on cases of keylogging in the 1970s involved government surveillance of electronic typing machines. Today,
keystroke monitoring software is widely available for commercial and personal use.
Do mobile devices get keyloggers?
Mobile devices can be monitored using keylogging applications. Some of these programs may be able to monitor
screen interactions, downloads, location data, and even conversations.
Can a keylogger be detected?
Keyloggers may be difficult to detect, but they are identifiable. The nigh common mode to notice a keylogger is
by searching a device'south software, applications, and groundwork processes.
How can I tell if I have a keylogger infection?
If your device has been infected by keylogger malware, you may discover arrangement lag, noticeable overheating, or the
presence of unfamiliar software, system processes, or browser extensions.
How can I protect myself from keyloggers?
One of the best ways to protect yourself from keyloggers is to refrain from downloading files or clicking links from suspicious emails, letters, or contacts. Enabling ii-factor hallmark is also helpful in preventing identity theft that may result from malicious keylogging.
How can I remove keyloggers?
If y'all detect a strange program that may be a keylogger in your browser extensions, system processes, or software list, remove it immediately. Browser extensions can exist easily removed from your list of extensions, and device applications tin can be deleted, moved to the trash, or uninstalled.

Cyber threats have evolved, and so have we.
Norton 360™ with LifeLock™, all-in-one, comprehensive protection against viruses, malware, identity theft, online tracking and much, much more than.
Try Norton 360 with Lifelock.

Editorial note: Our articles provide educational information for y'all. NortonLifeLock offerings may non cover or protect against every type of crime, fraud, or threat nosotros write about. Our goal is to increment awareness about cyber prophylactic. Please review complete Terms during enrollment or setup. Remember that no 1 can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses.
Copyright © 2022 NortonLifeLock Inc. All rights reserved. NortonLifeLock, the NortonLifeLock Logo, the Checkmark Logo, Norton, LifeLock, and the LockMan Logo are trademarks or registered trademarks of NortonLifeLock Inc. or its affiliates in the U.s. and other countries. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.South. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons iii.0 Attribution License. Other names may exist trademarks of their respective owners.
Source: https://us.norton.com/internetsecurity-malware-what-is-a-keylogger.html
0 Response to "Can a Screen Lock Pin Keep a Keylogger Out of My Phone"
Post a Comment